5 Ways to Fix Error While Deleting Key
Most advanced users know all about it, but if you didn’t know what the Windows registry is, it’s a several megabyte database that stores most of the information for your Windows operating system. It contains thousands of configuration settings for Windows itself, third party software, hardware and preferences for the individual users on the computer. Editing the Windows registry can be dangerous if you don’t know what you’re doing because if you wrongly delete an important key, Windows might not be able to boot up the next time.
So no matter how confident and experienced you are, it’s always a sensible idea to be a little bit safer and make a backup of the registry keys that you intend to edit, or even better, make a complete backup of the whole registry as well just in case. If you’re trying to edit or delete keys from the registry to repair or recover from certain problems, you might find that some keys won’t let you do anything with them and you’ll get an error such as “Cannot delete xxxxx: Error while deleting key”. These keys are usually protected to stop accidental deletion and it’s important you have the correct key before trying to change it.
You could also be the administrator on the computer, but still can’t manipulate the required key, which might sound quite odd. Even though the administrator account has a great deal of control, there are other hidden accounts and levels on the system which have even greater access and therefore standard administrator privileges are not enough. To solve this problem, you have to force the registry to allow the logged on user full control of the subkeys. Below are several different ways of performing this operation to give you the required access.
1. Run Regedit using the RunAsSystem toolAs well as being able to take ownership of registry keys and setting the permissions manually, another thing you can do is run the Windows registry editor with highly elevated privileges. This can be achieved with the System account that is even more powerful than the administrator and therefore has more access to protected registry keys. This has the added bonus of allowing you to view the SAM and SECURITY registry keys which are otherwise hidden. A small portable tool called RunAsSystem is able to do this for any program you tell it to, here’s how.
1. Download RunAsSystem, extract and run it.
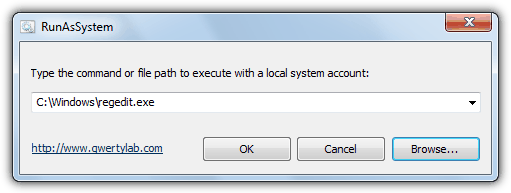
2. Click the Browse button and look for regedit.exe which is normally located in the Windows folder, or simply type regedit into the box.
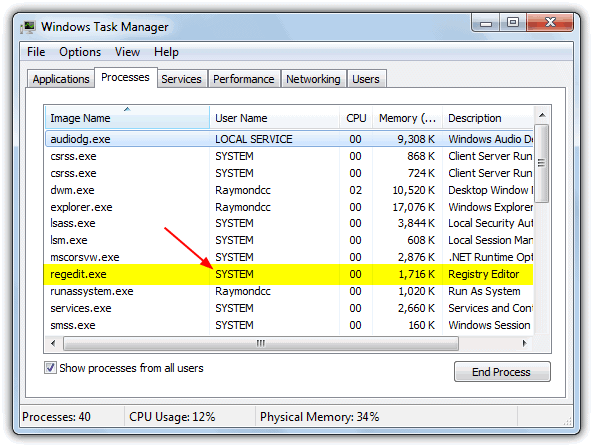
3. Click OK which will open the Registry Editor. If you open up the Task Manager, and as you can see from the screenshot below, regedit.exe is now running under the SYSTEM account where it would normally run under the user’s standard account. You can delete several legacy keys without the “Error While Deleting Key” message.
RunAsSystem is also useful if you want to restore any registry keys that were deleted this way because importing the keys would produce a “Cannot import file.reg: Error accessing the registry” message from the standard admin/user account. The solution is to either run regedit as System, and import it from File -> Import, or run the .reg file using RunAsSystem.
2. Use the PsExec tool
The PsExec command line utility is part of the PSTools remote administration set of command line utilities from Sysinternals. Like the RunAsSystem tool, PsExec also allows you to see the SAM and SECURITY keys that are hidden under normal circumstances. It works in a similar way too by elevating the registry editor to run under the System account granting more control over the registry. You need to make sure you have administrator privileges in the first place for this to work.
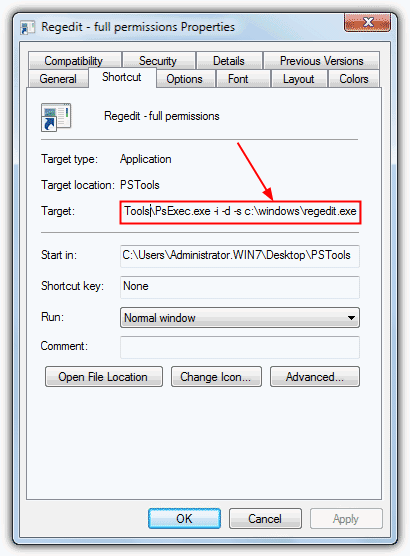
1. Download and extract the PSTools.zip file from the Sysinternals website. Right click on the PsExec utility and click Create Shortcut (or Send to -> Desktop).
2. Right click on the shortcut -> Properties and add the following to the end of the line in the Target box:
{space}-i -d -s c:\windows\regedit.exe
3. Click OK and then double click the shortcut to launch Regedit under the System account. If you’re still unable to delete or edit the keys you want, try the next solution below.
3. Registrar Registry Manager
Registrar is a registry editing tool with several advanced features and is a lot more like a standard Windows Explorer interface with toolbar buttons for back, forward, cut, copy, paste etc. It also has advanced searching and comparing functions, bookmarking, a registry defragmenter and a backup and restore option. There are other features such as multi level undo and remote registry editing, but they along with several other features are only available in the Professional version which costs around $55.
Thankfully there is a free Home Edition that allows you to browse and edit the registry without any problems, the only downsides are the nag screen and not knowing some functions aren’t in the free version until you click on them. Like the tools above it also shows the usually hidden SAM and SECURITY keys, and while testing it was able to edit or delete a number of the registry keys that the tools above couldn’t. Keys you would normally have to edit the permissions manually to delete such as those that need removing to repair the Features window problem in Windows Vista or 7 are done so with the click of a button.
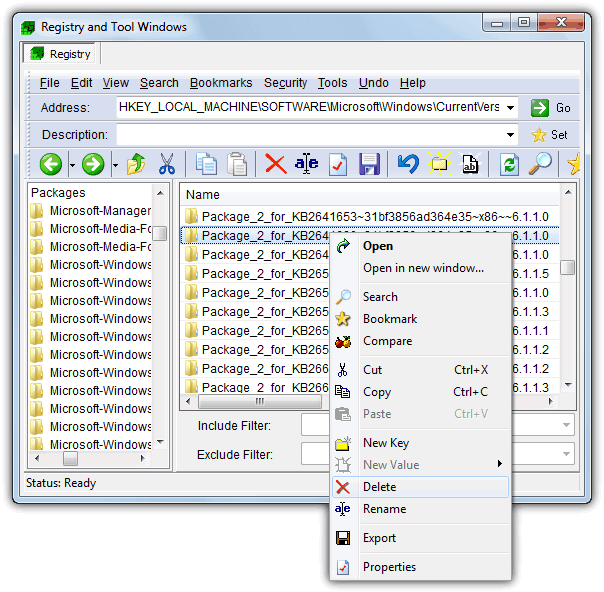
Usage is pretty much the same as regedit and you simply navigate your way to the required key and then right click on it or use the buttons in the toolbar to rename or delete etc. If manually editing registry permissions sounds to confusing, this might be your best option. Registrar can also be made portable by copying its folder from Program Files, and works on Windows XP up to Windows 8.
Download Registrar Registry Manager Home
If even these tools aren’t working for you, the next option will be to edit the permissions for the key manually using Regedit or simply use a low-level anti-rootkit tool. On page 2 we’ll show you how.
4. Manually Edit Registry permissions
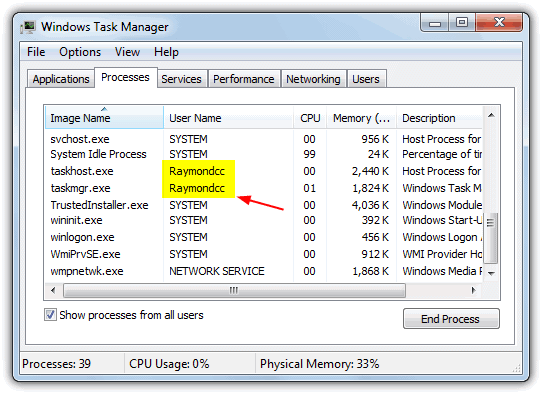
First of all, you need to make sure that your account has administrative privileges to be able to edit the registry. And secondly, to edit the restricted registry you need to know what the currently logged on user’s name is. You should know this but if you’re not exactly sure of the current user name, a simple way of telling is clicking on Start and looking at the top (XP) or top right (Vista/7) of the Start menu. Alternatively find out from the Windows Task Manager. Simultaneously press Ctrl+Shift+Escape, go to the Processes tab and check the User Name column. You should see SYSTEM, LOCAL SERVICE, NETWORK SERVICE and the logged on User name.
Now simply follow the steps below to take full control of a restricted registry key. There are thousands of protected keys in the registry with varying levels of restrictions, do not that not all keys can be deleted even using this method.
1. Run the Registry Editor by typing regedit in the Run box (Win key+R) or from the Start search box.
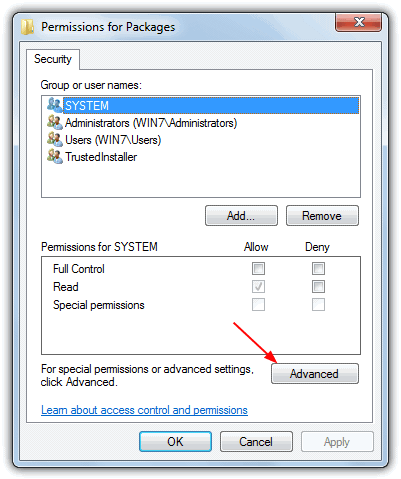
2. Navigate to the registry key you want to take full control of, right click on it and select Permissions. Then click the Advanced button.
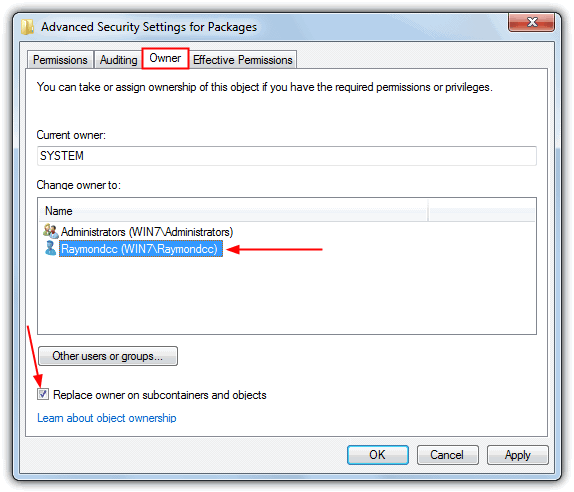
3. Go to the Owner tab, select the user name that the system is logged on with and tick “Replace owner on subcontainers and objects” and click OK.
4. Now you should be back at the Permissions window again. In Windows XP, click on Everyone and then tick Full Control for Allow. In Windows Vista and Windows 7/8, select the group which the currently logged on user belongs to (Administrators) and tick Full Control for Allow. Click OK.
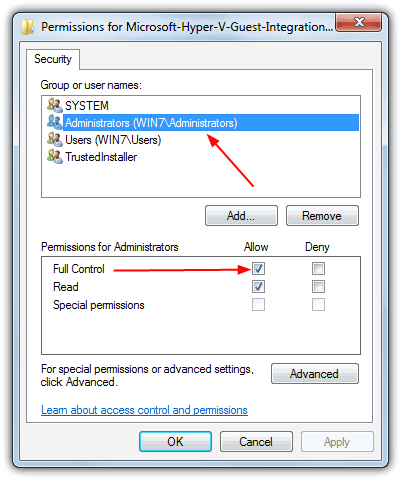
Now you can modify and delete the protected registry keys. Windows protects those registry keys from being easily modified for a safety reason, so make sure you know what you’re doing before messing with it.
Depending on which keys you’re trying to edit, the above steps still might not be enough and you’ll get “Error while deleting key” again with the Allow tick boxes grayed out. If that’s the case, follow these extra steps:
1. Click on Advanced again and in the window highlight the same user group from step #4 above.
2. Tick the “Replace all child object permissions with inheritable permissions from this object” box and untick “Include inheritable permissions from this object’s parent”. Click Add (or Copy for XP) in the warning popup and then OK. The grayed out Allow tick boxes should now be enabled and already ticked, now try to edit the key.
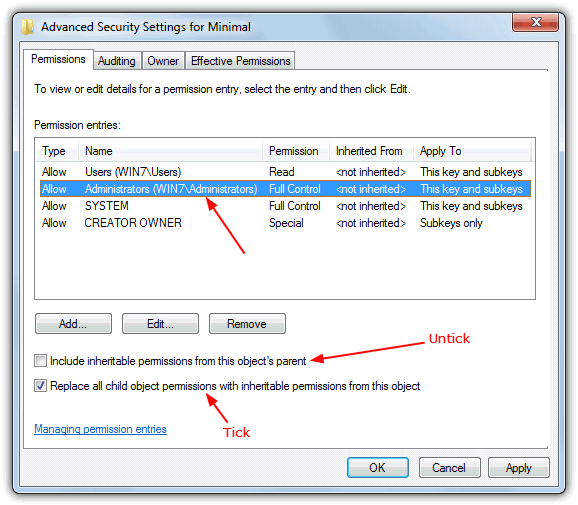
Unfortunately there are still certain keys in the registry which cannot be edited because they are in use and locked by the system. No amount of permissions tweaking will allow them to be touched. In that scenario the only other option may be to edit the registry while it is offline.
5. Using low-level anti-rootkit tools
Anti-rootkit tools are very powerful low-level utilities that is capable in detecting and removing rootkits. There are 2 of such anti-rootkit tools that comes with a registry editor which looks very similar to the Windows regedit except it bypasses the Windows restrictions to allow full control in deleting and editing restricted registry keys.
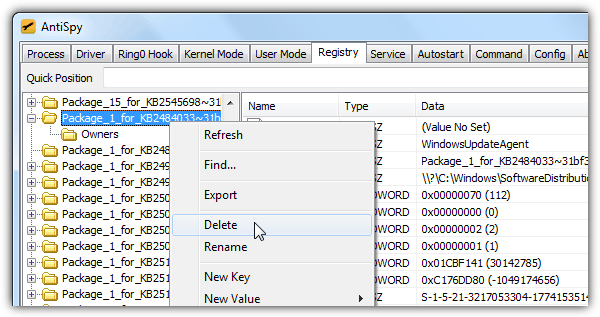
All you need to do is run either AntiSpy or PC Hunter, go to the Registry tab, navigate to the key that you cannot delete from the Windows regedit, right click and select Delete. The deleted keys takes effect instantly without requiring a restart.

“Registrar Registry Manager” is the truth. Thank you, sir!
Thank you very much! The tip on using PsExec was incredibly helpful for me!
This was the option that I chose to try first because I’m at least familiar with the SystemInternals Suite so I felt comfortable with it’s security integrity. Before this, I was totally unable to manipulate certain keys.
i tried to delete an unaccessable key (all permissions was deleted) with Registrar Registry Manager program
AND IT REALLY WORKED !!
many thanks…
Thanks a bunch
The RunAsSystem Tool slapped those oldies down and out.
Very Simple
After trying MANY tools to delete an invlaid Registry key, including Sysinternals (MS) Regdelnull, I finally downloaded RegistrarHomeV8. It completed the job on the first try.
Thank you for this article and the citations!!
Thankyou So much. Runassystem worked for me.
Registrar worked for me!
This tool “RunAsSystem tool” works great. Thank you.
Worked perfectly. Thank you so much!
How to Uninstall “RunAsSystem tool” from the PC?
After work done!
Thanks a lot!
RunAsSystem tool worked for me.
I was unable to delete Bluestacks key. But it worked for me.
# Keep Posting. :)
wow,the manual permission is really working on me,thanks man,i really like all of this method :)
The RunAsSystem tool worked flawlessly, I’m really thankful
Thanks, but when you will execute the psexec run as administrator. ;)
After going round through the internet with no vain. Registrar Register Manager worked like charm. Thanks to u
thanks a lot…you saved me a lot of trouble.
PC Hunter works like a charm for me!
Thanks a million! Tried all your suggestions and the third one worked for me.
youre awesome after hundred of useless tries i finally deleted it thanks man thanks to your run as system tool
I cannot get the “Run as system” to work! I still get the “error while deleting key”
Any other ideas?
That’s why we give you 5 methods to try, if one doesn’t work, move onto the next.
Check this out. It’s similar to RunAsSystem but much better.
sordum.org/9416/powerrun-v1-1-run-with-highest-privileges/
THANKS IT WORKED I USED RUN AS SYSTEM TOOL
Thank you so much. perfect
I used the RunAsSystem tool…..but I still had to change the owner of the key to ‘SYSTEM’ user before I could successfully delete the key. I suppose I could have changed it to ‘everyone’ and it should have worked also. In any case, thank you.
Thank you! the RunasSystem helped me delete the keys I wanted
Registrar Registry Manager helped. Thank you
Thank You. I did delete the registries made by virus. i used Registrar Registry Manager.
I don´t speak English, bat i understand more or less and all ok. thank you.
This completely worked, thank you! You might want to note that you MAY need to adjust the registry permissions of the key if it doesn’t let you delete it. My SYSTEM account did not have full rights but i checked the checkbox and added it for each key, then deleted them.
Perfect..! RunAsSystem method worked for me perfectly. Thank you for your efforts. Thank you very much.
Thank you so much!
Method 1 & 2 didn’t work but 3. Registrar Registry Manager works perfectly!!!!
Thanks, I used your advice to manually take ownership of a registry key that would not delete. An error message appeard in the key identified by CCleaner as not responding. I changed ownership and deleted right away. Good advice, thanks. BC
If still not able to delete the key, change its permission for Administrator with Full Access right first. Then try delete the key again.
RunAsSystem worked for me as well, but I also had to rename the keys before it would allow me to delete them.
Thanks,
Yes, It worked with RunAsSystem.
Cheers…! :)
Thank you for the effort! Changing the permissions didn’t work. However PCHunter did the excellent job. Deleted registry entries (leftovers from MS Office) without a problem.
Windows 8.1 64_bit
I love to use PCHunter for my win 8.1pro. iolo 12.5 blushed me when i was removing a registery folder along with sub containers with error “Cannot delete:error while deleting key”. Million Thanks for the article and the companies who introduced the tools to solve our problems on the fly.
Thank you! Thank you. The regedit “Run as System” utility allowed me to delete that nasty and annoying “FindingDiscount Adware.
YAY!! Thank You!!!– this was most helpful and valid for my Win7 Pro box.
Thanks for this very useful tutorial. PC hunter which is working on a 64 bit system and windows 8.1 was the only tool that allowed me to modify a value. In order to disable the service of Windows Defender.
But this program was marked as a maybe dangerous program by my antivirus Kaspersky.
pc hunter was the only thing that would get rid of isafe and yac registry entries. thanx a million
The RunAsSystem utility solved my problem. I found that even taking ownership and granting permissions wasn’t enough to delete the registry keys I needed to; I had to rename them first. Stupid and annoying, but true. Try to delete > fail. Rename > try to delete> succeed.
Hey Raymond,
As somebody pointed out earlier you deserve to be give an out of turn promotion to Sainthood…. :-)
Can’t thank you enough. Been trying to remove some registry settings from a nasty spyware. Nothing else worked until I used RunAsSystem. Worked like a charm.
+1 PC Hunter worked for me as well
Thanks a bunch :) PCHunter was very helpful.
THANKS!! The ONLY solution that worked for me on XP was PCHunter Free.
Many thanks. PC Hunter did the business, when AntiSpy would not. I did not try a boot disk solution, but apart from that nothing else would work.
Thank you so much! I’ve been spending my entire day on trying to remove stubborn nqij.exe registry entries! Registrar Registry Manager managed to delete them!
Thank you!!! I had a pesky key whose SYSTEM principal was keeping the key owner from having full control. RunAsSystem worked wonderfully. Why is Windows such a PITA compared to UNIX for system control?
Thanks you for Registrar Registry Manager !!!!
worked like god ‘ boon..regisrar registry mechanic free edition up to yhe mark…..thank you …
Even I a 73 year old OAP was able to follow your instructions and issues with avast legacy keys now resolved
many thanks
Thanks a million !!! Worked like charm :-)
Thaaanks so much, Raymond!
That helps me a lot..
Frankly, I was quite desperate when I receive message like “…cannot be opened. An error is preventing this key from being opened. Details: Access is denied.” . I thought I should recover with kinda sophisticated software. Bu then, I ended up choosing run as system software, aand my proble solved. I can reset the permission in the register subdirectory. Sooo much worth for a 281kb file :)
simply in one word you are awsome for people like us. great really great. one question how these tools works
THANKS A LOT ………I really mean it………i have been struggling throughout the day on deleting …ur post was very helpful
THANKS!!! Finally my trojan downloader is removed, nqij.exe
3rd way solved my problem :) :)
Amazing – I used PC Hunter’s registry editor to disable Symantec’s antivirus context menu key, which I had been unable to do by any other method because I could not change the key permissions. I didn’t really expect PC Hunter to do any better, but I could edit the key straight away – how do you do that?
Anyway, many thanks for making this possible – got rid of the pesky context menu entry at last.
Thanks a lot for suggesting PCHunter: the only way I managed to delete these keys!
Thank you so much!
If I will have discovered this topic earlier, it will have saved me few hours *sigh*. Thanks bro, the first recommendation works prefectly fine.
thanks man you are the best
RunAsSytem Worked on Win7 64bit
Works flawlessly, THX!
Thanks Raymond, PsExec did the job! I had *almost* given up getting rid of these troublesome entries.
Thanks again, now I’ll sleep better tonight ;)
you made my day a better day thanks
Thank you its working fine :)
I’d taken out Comodo Firewall on a Windows 7 Home Premium 64 bit last week, and was going stir trying to get legacy keys out (all BUT driver inspect.sys and legacy keys removed by usual uninstall)…nobody else had the right permissions description, but I tried YOURS on all CF legacy keys in one sitting, rebooted, and BAM! All those enum legacy keys stopped regenerating! You keep things not only easy, but fast and bang-on! Thank you!
Thank you so much the only solution that works!
Great man… Very Good THANK YOU ! !
Totally genius! Big THANK YOU
Raymond…you are the MAN! It worked just as advertised. THANKS!!!!!!!
many Thanks !!
Thank you very much! This saved me an enormous amount of time!
Thanks very much.
It worked perfectly fine on windows 7.
thanks a lot buddy it worked for me
I had forgotten how – thanks for reminding me.
You are THE MAN
Wow !! Thanks !! Works Perfectly… :)
Thanks – this helped me out as well. I tried doing an upgrade install with slipstream disk for Vista SP2, but couldn’t get that to work. I deleted registry keys found in checksur.log and Windows feature box came up with info finally
Thanks so much. I thought I completely messed up with the registry of my pc.
THANK YOU SO MUCH!!!!!!! trying to fix this all night,,, i love you man
Thanks a ton to the above poster. This got me out of the registry mess I was in. Sysinternals is awesome.
Ray,
I normally don’t reply to these posts but… Thank You!
I need to be able to manage 2008 group policy modifications from my windows 7 machine because or 2003 group policy management server isn’t able to manage some new schema functions.
But you got me in business with your post.
Thanks again!
It works in Windows 7.
Thank you very much Raymond!
Thanks this worked for me
Been looking for a solution like this for far too long, never thought to check that box, thanks for the fix!
Thanks Raymond.
Nice info.
Thanks a lot. This is very useful info. I’m sure I’ll need to do this one day…
ever since the live help & support been going on, this blog has been very much useful indeed… keep on the good work. now i can learn a lot.
Thank you Raymond
interesting,and protective
thanks.
good info….thanks Raymond
Wow, the keys to the kingdom for anyone to use. That should be fun..
Thanks for the info.
“Who dares,wins”
Anonymous.
This post is great because I was never able to delete legacy keys.
People who I have told about you say that’s unbelievable what you are doing for computer novices.
Nice, thank you Raymond. :)
good info