6 Ways to Remove Fake Antivirus Software: Quick Guide
4. Malwarebytes Antimalware and Chameleon
The Malwarebytes software is perhaps the most well known and popular software for removing just about all types of fake antivirus, fake hdd scanners, fake police ransom software and much more. The good thing about this program is it can remove and restore to normal most changes malware like this leaves behind such as bogus registry entries, alterations to the system settings such as file types or policies, and leftover files etc.
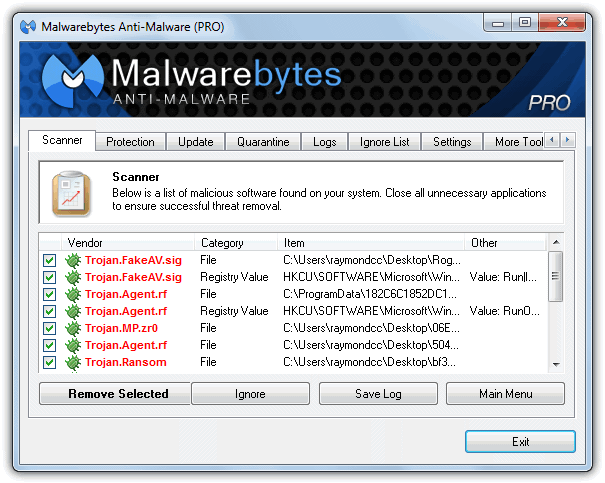
Malwarebytes Pro can protect your system from rogue software installing itself in the first place, but the free edition is an on-demand scanner only which can clean up the mess left behind after an infection. As such, you need to be able to get the free version installed after either killing the rogue process from another program that can terminate the process such as RogueKiller, RKill or Process Explorer for example.
Another option is using the Malwarebytes Chameleon tool which is designed to get the Antimalware application installed and running while any rogue or fake antivirus software is still active on the system and preventing a normal install. The zip contains differently named files which are actually the same file just with different extensions to help get around any block. The tool will attempt to kill any rogue processes, then automatically download, install and run a scan with Malwarebytes Antimalware. This method isn’t foolproof though and some rogues can still block the Chameleon tool from running such as the Smart/Internet Security fake antivirus when we tested it.
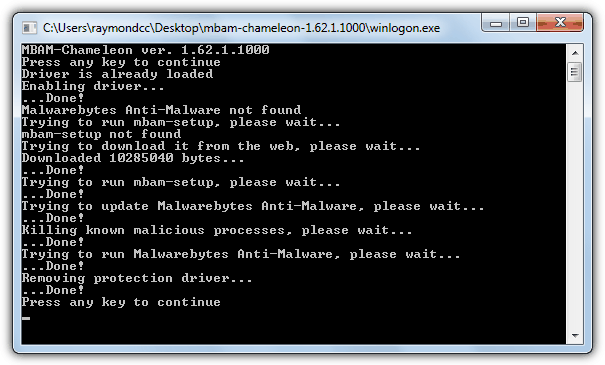
Malwarebytes Antimalware is a valuable program to cleanup the after effects of rogue or fake software and should also be run after tools like RogueKiller and RKill have been used to remove any remaining remnants and get your system back to normal.
Download Malwarebytes Antimalware
5. Process Explorer
While it’s true Process Explorer is not a fake antivirus removal tool in itself, because most fake rogues disable Windows Task Manager so you can’t easily kill them, using a third party task manager tool such as this can help you quickly disable the rogue process allowing other tools like Malwarebytes to install and clean up the mess. Of course, if you prefer Process Hacker or a different tool, that can be used as well.
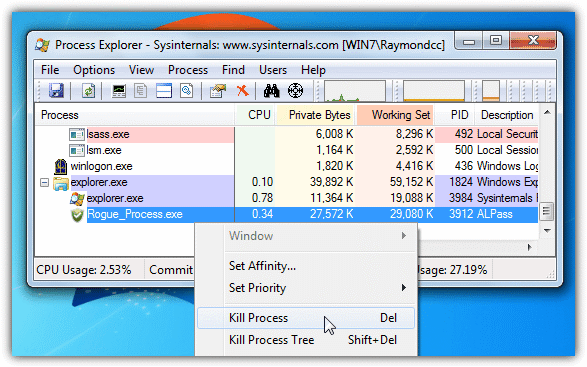
It’s quite likely that the Process Explorer executable you download (Procxp.exe) will not run as exe file launching probably has been disabled by the rogue program, renaming it to Winlogon.exe, Explorer.exe, Userinit.exe, Wininit.exe or Iexplore.exe will likely solve the problem. This is probably due to the fact that the fake program has to allow the real files with those names to run or windows won’t boot properly to the desktop allowing the fake nag messages to show. Finding the rogue process is usually quite easy as it often has an obscure or random character name and will be in the explorer.exe process tree. Then simply right click on it and select Kill Process. After that, you can install a Malware scanner or run your resident security software to clear the remains.
6. Remove Fake Antivirus
We thought the Remove Fake Antivirus software is worth a quick mention because you will sometimes see it recommended to remove a piece of fake antivirus software from various sources on the internet. Unfortunately, the program is out of date these days and quite ineffective against most rogueware produced in the last couple of years, not detecting the System Doctor 2014, System Care or Smart/Internet Security rogues we tried. It still might be capable of removing the problem if what’s infiltrated your machine isn’t brand new though.
Although the utility itself has limited usage, the Free of virus website that created it still has lots of useful and more recent information about how to manually remove newer fakes including those we mentioned in the previous paragraph.
Download/Visit Remove Fake Antivirus
Some Quick Tips to Help Remove Fake Rogues
Although the methods above should be more than enough to remove just about all fake antivirus or fake hdd scan software currently around, if you come up against a more aggressive rogue where they don’t work or still having issues removing the fake process, there are a few other things you can try to get around the problem:
These fake programs are nearly always user specific, meaning that it will only affect the user account that installed the rogue in the first place. If you have more than one account on the computer, simply switch to another user and it should be unaffected meaning you can install or run scanning software from there to remove the threat. You can also go to Control Panel and create a new account from an infected account if you’re the only user.
As they are mostly started by using the Run or RunOnce registry keys, you can easily bypass most rogues by simply booting into Safe Mode (F8). Third party applications that normally start with Windows are ignored while booting to Safe Mode and this includes the fake antivirus software meaning you can simply run a removal tool or manually remove the threat from there.
A simple tip if you’re a User account and not Administrator is to right click on the program you want to run such as RogueKiller or RKill and select “Run as Administrator”. This has an effect of elevating your privilege level above that of the the fake program so you can run the executable file.
As we’ve already mentioned, renaming the executable file you’re trying to run using something like Winlogon.exe, Explorer.exe, Userinit.exe, Wininit.exe or IExplore.exe often bypasses the rogue program and allows the executable to run. Just changing the extension to .com or .scr has little effect these days with the latest rogues. This won’t work though if the renamed executable calls another executable file because that one will be blocked.


I have tried both both Malwarebytes & Superantispyware but it didn’t resolve the problem but the RogueKiller tool did it all. Thanks for the suggested tools and it is really helpful
The number of times I’ve run into the fake antivirus malware on my and other peoples systems beggers belief… I just wish I could get my hands on the cockroaches that develop this infestation..
Thank god something like this came out. I work as a tech at a major university in the technology building. The Rtard teachers constantly get these stupid things. It makes me laugh that the teachers in the COLLEGE OF TECHNOLOGY manage to get these. At least twice a week Ill have to get one of these fake anti viruses off.
I suggest you only use Malwarebytes as it is a fantastic free software that removes much more than the Fake Antivirus software and will not cause any side effects on any operating system,
Wooh this is great software.Thank you Raymond
it really works………
i tried too….
many many thanks to you……
Great tip, Raymond!
I usually prefer to use Super Anti Spyware. It covers both rogue antiviruses and other kinds of spyware. The free version offers cleanup and the pro version offers realtime protection as well as other features.
Interesting find, nontheless :)
i used Superantispyware it removes and i’ll try this Fake antivirus thanks Raymond …
Hey Ray,
Thanks for this great post again as it really help my friend’s computer in removing the fake anti-virus.Kudos !!!
thanks for the info ray! :D
use malwarebytes guys… it really knows how to destroy fake antivirus
It’s also an amazingly fast download too!
I clicked on the link to download, and first thought, “nothing happened”, then checked my download file.
Yep! there it was!
Thank You Raymond!
Steve
cool … just with file size 83k only!
Nice one to give it a try.
Thanks Raymond for sharing this.
amon
thanks Ray…
nice tool. thanks.
thanks ray……..
really great information Ray
thank you ray ,thats going straight on my usb stick
Very useful ray.
Good one, Ray…
Wow..nice to know..Thanks for sharing Ray.
thanks Raymond
Thanks Ray for this important advice.
And also thanks for the guy from Malaysia – Olsen – who developed the software Remove Fake Antivirus.
good info ray. thanks
thanks good one